Introduction
Bruter is a lightweight application built as an experimental project while learning the Go programming language. Though inspired by the popular Xray tool from GitHub, Bruter introduces its own set of features, tailored specifically for web server testing and configuration validation. Whether you’re a seasoned web administrator or a beginner in cybersecurity, Bruter offers a streamlined way to assess various aspects of web servers with a user-friendly interface.
In this blog post, we’ll explore what Bruter does, how it works, and why it might be an essential addition to your web server auditing toolkit.
GitHub repo can be found here Bruter
What Does Bruter Do?
At its core, Bruter serves as a versatile web server testing tool. Here are the primary functions it performs:
-
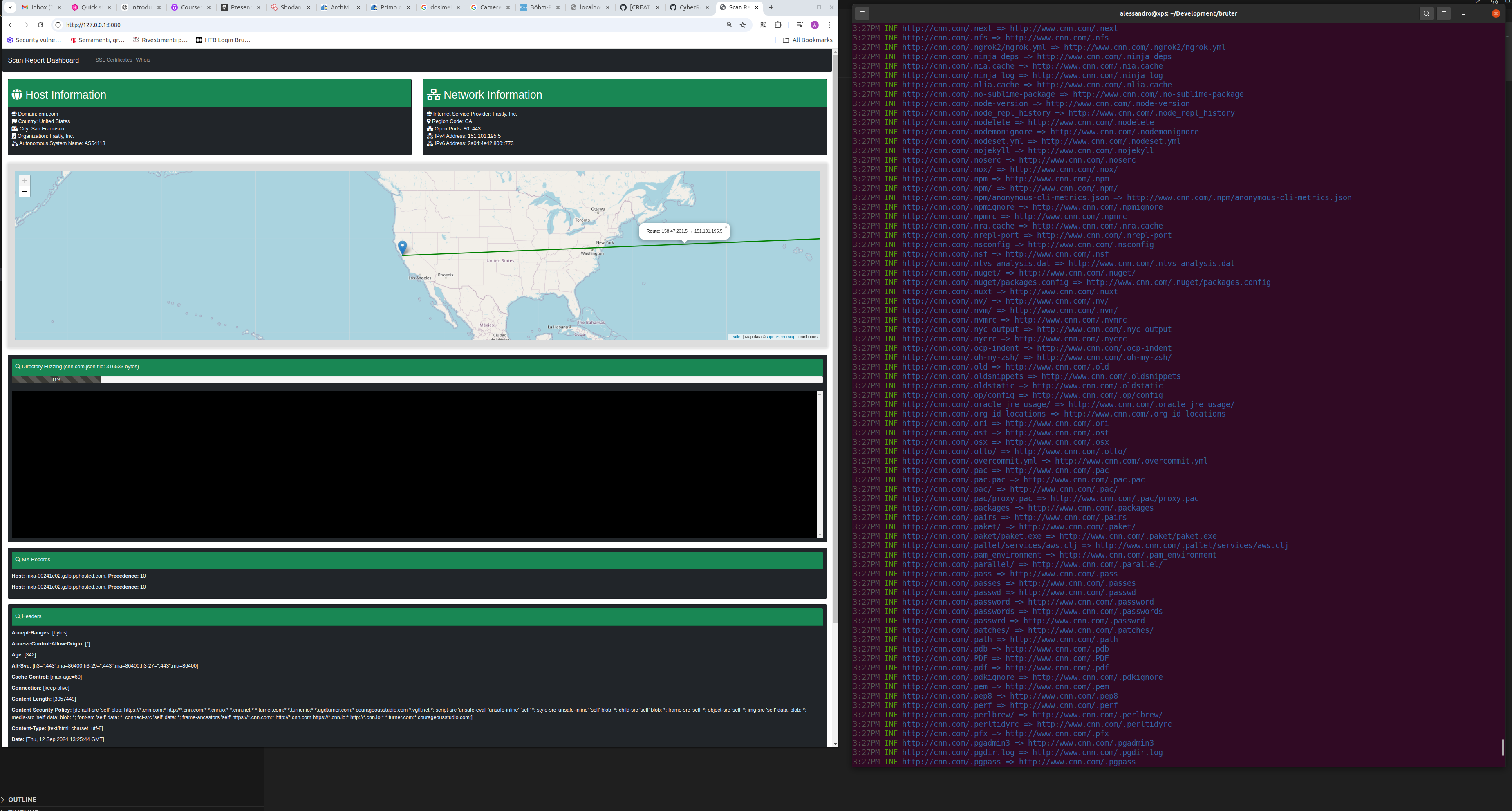
Shodan HostInfo Data Collection Bruter leverages the Shodan API to gather HostInfo data, which provides detailed information about a target server’s configuration and vulnerabilities. To use this feature, you’ll need to obtain a Shodan API Token. With this token, Bruter can query Shodan for crucial server data, enabling security professionals to assess the server’s exposure to the internet.
-
Service Banner Collection Bruter automatically collects banners for various services running on the target server, such as: FTP, SSH, MySQ, IRC, SMTP. These banners provide details about the services’ versions and configurations, allowing testers to identify potential vulnerabilities or misconfigurations that might be exploitable.
-
HTTP Header Collection Bruter can extract HTTP headers from the target web server, giving insights into how the server handles web requests. This can help reveal important server-side settings, security features (or lack thereof), and potentially outdated software versions.
-
WHOIS Query Information Using built-in functionality, Bruter performs WHOIS queries, providing information about domain ownership, registration dates, and contact details. This can be useful for understanding the context of a target web server, especially when assessing a large number of assets in a penetration testing scenario.
-
Directory Brute Forcing Bruter’s directory brute forcing feature allows it to scan for common directories on web servers. By using brute force techniques, it identifies directories and returns results for HTTP status codes such as 200 (OK). This feature helps uncover hidden or forgotten directories that could potentially contain sensitive information.
-
SSL Certificate Information Bruter queries crt.sh, a service that tracks SSL certificates issued by trusted certificate authorities. This provides users with information about the SSL certificates being used by the target server, including expiration dates and potential misconfigurations in certificate management.
-
Custom Wordlist Support Bruter supports custom wordlists for directory brute-forcing, allowing users to tailor their testing according to the target server’s structure. This flexibility is particularly useful for specialized testing environments, where default wordlists may not be sufficient to uncover all potential issues.
-
Custom extensions Support custom file extensions during brute force directory scanning. By using the -extension flag, users can specify the type of file extension they want Bruter to focus on, with the default being JavaScript files (.js).
-
Web UI for Results Presentation To ensure ease of use, Bruter provides a Web UI that presents the results of all tests in an organized, user-friendly manner. This feature is particularly helpful for visualizing data, making it easier to interpret findings and share them with stakeholders.
Why Use Bruter?
While there are many tools available for web server testing, Bruter offers several unique advantages:
Lightweight and Easy to Use: Bruter is built as a simple tool in Go, making it efficient and easy to run. Whether you’re a beginner or an expert, the Web UI makes navigating the results straightforward. Combines Multiple Functions: Bruter isn’t just a one-trick pony; it integrates multiple testing functions (banner collection, brute forcing, SSL info, etc.) into a single tool, simplifying the process of web server assessment. Customizable: With support for custom wordlists, Bruter can be tailored to specific environments, providing flexibility and precision in testing. Great for Learning: If you’re interested in learning more about Go or how web server testing tools work, Bruter’s source code offers a clean and practical example of how to build a robust tool from scratch. Getting Started with Bruter Prerequisites
To get started with Bruter, you’ll need:
A Shodan API Token to access HostInfo data A Go development environment to compile and run the application is provided with a Dockerfile. Custom wordlists if you want to use tailored directory brute-forcing
docker build -t bruter .
docker run --rm -it -p 8080:8080 bruter -domain example.com -shodan [shodanapikey] -verbose
Conclusion
Bruter is a valuable project for anyone looking to experiment with web server testing while learning Go. Its integration with tools like Shodan and crt.sh, combined with its multiple scanning functionalities, make it a convenient tool for quickly assessing the state of a web server. Whether you’re a developer or a security professional, Bruter offers a great starting point for web testing experiments.
If you’re eager to try Bruter for yourself, give it a go! It’s a great opportunity to not only learn about web server configurations but also explore Go’s capabilities in real-world applications.